If you shopped at a Target retail store in the US between November 27 and December 15, 2013 using your credit or debit card then you should demand a new card from your bank no matter what excuse your bank gives. Here are the simple reasons why. Continue reading
security
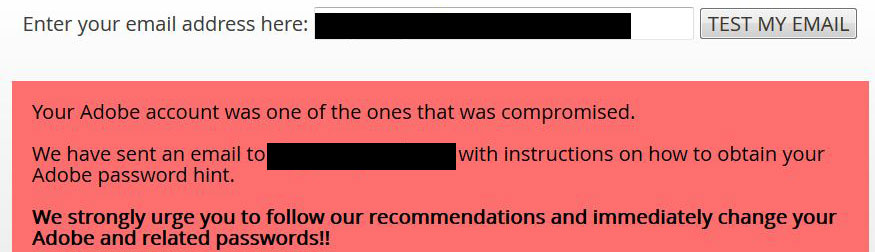 Recently Adobe was the target of a successful intrusion and data theft that resulted in the compromise of millions of accounts, encrypted credit cards, source code and who knows what else. The nice people at LastPass (the greatest password security product ever produced by humankind) have put together a great tool to tell you if your account was hacked and what you can do about it. Continue reading
Recently Adobe was the target of a successful intrusion and data theft that resulted in the compromise of millions of accounts, encrypted credit cards, source code and who knows what else. The nice people at LastPass (the greatest password security product ever produced by humankind) have put together a great tool to tell you if your account was hacked and what you can do about it. Continue reading
Since the NSA’s extensive domestic and international monitoring was revealed by Edward Snowden via The Guardian’s Glenn Greenwald in June 2013, much ink (or many pixels, as the case may be) has been spilled discussing whether or not the NSA has gone too far, whether the programs are unconstitutional, and a variety of other issues.
One view that I have not yet seen is that of someone on the front lines of information security, who deals with many of the threats that the NSA has been monitoring on a fairly regular basis.
Someone like me. Continue reading
If you run a WordPress blog you may have heard about the brute force password attacks that have been going on for a few months now. If you haven’t then there’s a pretty good chance that you’ve done nothing to protect your site and Russians control your site.
Up until today the attack has focused on the “admin” username and trying to guess the password over and over. In a sign that the attacks are continuing and evolving we noticed a slightly updated tactic of guessing the password for an accounts called “adminadmin” and “administrator.” Continue reading
 China’s been up to some shenanigans this week, no? Actually, China’s up to shenanigans every week but it doesn’t usually make the news. Regardless, it’s a good time to review your internet security practices! Kind of like when the neighbor’s house burns down and you go through your apartment checking all your smoke alarms and fire extinguishers for the first time in two years.
China’s been up to some shenanigans this week, no? Actually, China’s up to shenanigans every week but it doesn’t usually make the news. Regardless, it’s a good time to review your internet security practices! Kind of like when the neighbor’s house burns down and you go through your apartment checking all your smoke alarms and fire extinguishers for the first time in two years.
So today, let’s talk about passwords. We all have them! Probably far more than we’d like to have. They’re also just about the only thing standing between us and A Great Big Bad Day. Getting your online accounts hacked sucks. Just ask Anthony Weiner. Continue reading
Twitter finally gives you the option to use full time HTTPS. This will encrypt all of your traffic between your computer and Twitter’s servers making it more difficult for people to intercept or hijack your session with Firesheep or other tools.
- Login to Twitter
- On the upper right you should see your avatar and username. Click this.
- Select Settings
- Click the check box next to “
- Click Save
- Enter your password to verify
That’s it, now you use HTTPS all the time. Keep Tweeting those Crasstalk stories.
Source and screenshot Engadget.
Hacking is usually an ‘underground’ sport, something nerdy Eastern Europeans do in their mother’s basements. The only time a hacker would come together to meet another hacker would be on an IRC channel. Not so anymore, with conventions like Defcon, Blackhat, and CanSecWest.
CanSecWest has an interesting contest. A hacking contest. The targets are the most common browsers: IE, Firefox, Chrome, and Safari. A new feature this year is the addition of smartphone hacking: Apple iOS, Windows Phone 7, Google Android, and BlackBerry OS. In total there is $125,000 in cash prizes. Another cool aspect of the competition: if you hack the computer running the target browser, you get to keep the laptop.
Like any good contest, there are the favorites. Charlie Miller, a software analyst from Baltimore has won the contest 3 times before. In 2009 Miller took down Safari running on an Apple in 10 seconds! He scored $10,000 and a laptop for his troubles. “Nils” (The contest allows anonymous entries) – a German computer science student, won last year, cracking Firefox, Safari, and Chrome in less than 10 minutes. In 2009, Nils broke the encryption for IE 8 the day before it was released, netting a new Sony laptop and $5k. George Hotz, the 21 year old who broke the Playstation 3’s copy protection (not to mention being the first person to ever jailbreak the iPhone) will be competing this year.
The biggest challenge this year is Google’s Chrome browser. Chrome runs in a ‘sandbox’ mode in Windows (basically insulating bugs in Chrome from affecting the underlying Windows system.) Google has put up $20,000 if someone can break Chrome’s sandbox mode in the first day.
Contests like this just aren’t cool in the computer security world. They provide vendors with information on how to improve the security of their products. When someone hacks a browser/device they also share technical information on how they did it with the contest organizers, TippingPoint. Details on the hacks aren’t released to the public until the vendor has time to fix the bug.
Pwn2Own runs during the CanSecWest conference, being held in Vancouver CA between March 9-11 2011.
Are web 2.0 services like GMail, Facebook, and bit-torrent really making it harder for the FBI to wiretap people doing illegal things? Do they need congress to pass a set of laws to aid them in capturing someone who uses Facebook? As someone who works computer forensics with law enforcement agencies, I’d say no. Its not enough for them to get your data after a wiretap, they want it now!
Sure, if data lies on Facebook’s servers and not your local hard drive, the feds will have to get a separate warrant/subpoena for those locations. The government already can wiretap your e-mail using the Communications Assistance for Law Enforcement Act (CALEA).
CALEA requires telcos and ISPs to turn over real-time monitoring to the feds if they are presented with a wiretap order. If the FBI had it their way, when those providers get the wiretap order authorities would not only have access to your real-time data, but also everything stored remotely.
So you might not be updating your pics on Facebook, but since you logged in anyway, they’d have access. Its a scary thought that everything online would be this accessible. Compound that with the risk of warrantless wiretaps and it’s enough for normal people to be concerned about their privacy online.
The feds know how much they can push, though. They’ve decided that the best way for them to address real-time wiretaps is through a shady program known as “Going Dark.” It’s shady enough that the Electronic Frontier Foundation had to file a freedom of information act request to find out any info on it.
This program aims to offer “incentives” to software developers to join their program. What incentives they’re offering, they don’t say. This week a software security company was hacked and it was revealed that the government was paying them to write backdoors into software for them. Microsoft has long been accused of having a backdoor in all of their products for the NSA.
I’m guessing that the FBI is asking, politely, for similar things. I don’t know what incentives the feds could offer a company, but since the “Going Dark” program is multi-agency and spans defense, law enforcement, and the Department of Justice, they could offer all kinds of under-the-table deals that we’d never hear about.
One of the problems we’re going to face in the future is that the government has no real standards in terms of computing. One agency will run one piece of software, another will run a completely different piece, on a different platform. The government also gets bilked by IT companies. I’ve seen broke school districts paying $2,000 for a Dell workstation because that’s what their contract says they’ll do.
I’m sure the different federal agencies work in a similar fashion. I’ve given presentations at law enforcement seminars where the previous speakers were standing up and teaching computer crime units on how to use Google. (As in, “put what you want to search for in the text box, click “search!”) And while I’ve given presentations where people actually know what they’re doing, the majority however have no clue. The people who are dreaming up these projects are trying to win support from people who have absolutely no clue when it comes to technology.
Privacy might not be a major concern for you now, but if programs like “Going Dark” get slipped under the radar its going to be too late for any of us to have privacy online ever again.
Note:
Here’s resident IT security expert bens and his analysis of the Gawker hack. He also has some tips for how protect yourself when stuff like this happens….
Gawker media got hacked, and in the hack Gawker’s master password file was stolen. What does this mean to you? Well, if you have linked any e-mail address that has any sort of real-world relevence to you to your Gawker account, you should change your password immediately. The same goes for your passwords. There’s a concept called “password entropy.” That is, if you use a login/password for one website and its compromised, you might use a similar login/pass on another site.
Change your passwords, and make sure they’re dissimilar from other passwords you’ve used.
Insofar as the “hack,” it looks like a script kiddie was looking for notoritety. From the released info, it appears that simple measures like having mildly secure passwords were not adhered to. Does it surprise me that between the Gawker Media Network there are machines running potentially inseucre software? No.
What is surprising is that even the site owner is using an eight character-long numeric password. Hey Nick, “24862486” might be a really easy password to remember, but dude, you’re running a media company with a huge online presence. You couldn’t tell me that a password like “N1ck$$d3nt0n$$$$$” isn’t a much better password that would be pretty easy to remember (its your name, with vowels as numbers, a couple non-alphanumeric characters, and its nice and long.)
A lot of brute-force methods won’t try to brute-force non alphanumerics, so signs like “$” and “!” and even more esoteric characters can slow down a brute force attack. However, if the password file is stolen it’s only a matter of time for it to be decrypted and all passwords revealed.
So what should you do? I know most of you are not technical users. The main thing you have to worry about is someone reading that your email address/password linked to Gawker is the same email account/password linked to your bank account.
So, change your bank password. Change your email password. Use multiple e-mail accounts so that if one is hacked, potentially you can compartmentalize the damage. If your bank statements go to your Gmail account, but you use a Hotmail account only for web forum passwords; you’re going to be much less exposed to risk if there’s a security leak.
Use strong passwords. Don’t rely on your password to remain secure. Change it every couple of months. Keep your software updated. If there’s a popup when you start your computer telling you that there’s a “critical software update” … download and install it! No computer system is 100% secure, but there’s a lot you can do to minimize damage.
Oh, and Gawker… who’s running your security policies? I’m not doing anything next week. Send me an email and lets run a pen. test. Were you guys running any IDS? You’re probably on the phone to the FBI right now and getting the run-around. You guys have my email address already!
