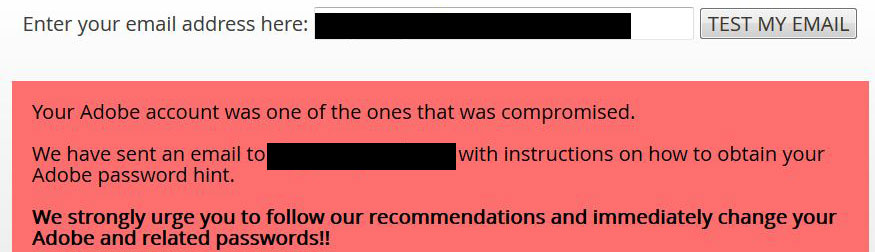
 Recently Adobe was the target of a successful intrusion and data theft that resulted in the compromise of millions of accounts, encrypted credit cards, source code and who knows what else. The nice people at LastPass (the greatest password security product ever produced by humankind) have put together a great tool to tell you if your account was hacked and what you can do about it. Continue reading
Recently Adobe was the target of a successful intrusion and data theft that resulted in the compromise of millions of accounts, encrypted credit cards, source code and who knows what else. The nice people at LastPass (the greatest password security product ever produced by humankind) have put together a great tool to tell you if your account was hacked and what you can do about it. Continue reading
Hacking
As the headline says, passwords to headhunting-slash-social-networking site LinkedIn and “headhunting”-slash-“social networking” site eHarmony have been hacked and are in the wild. A hacker posted files with literally millions of passwords to these sites in public, asking for help.
Security experts say that the hacker probably has many more passwords than he or she posted, and was just asking for help cracking the stronger ones (or subtly boasting about it). To be on the safe side, assume that this hacker and others by now have ALL LinkedIn and eHarmony passwords, and change yours (and if you used the same username and password on other internet sites, change it there too). Continue reading
After spending more than eighteen months of pre-trial confinement in a military prison, most of it under “maximum custody,” alleged WikiLeaks source Bradley Manning has finally begun the judicial process in a military court.
In the second day of his (UCMJ) Article 32 pre-trial hearing, it was revealed that the affidavit that served as the basis for his arrest appears to have been based in large part on unconfirmed or erroneous information.
Last night, a hacking group by the name of Lulzsecurity hacked a private company called Infragard. Infragard contracts with a bunch of government agencies like the FBI, the DoD, and multiple intelligence agencies. Supposedly the big thing that Infragard was working on was trying to take control of compromised Lybian computers, and set up a command and control interface for a botnet, for the DoD. Infragard had a lot of other contracts with government agencies, consulting on security practices.
Continue reading
Hacking is usually an ‘underground’ sport, something nerdy Eastern Europeans do in their mother’s basements. The only time a hacker would come together to meet another hacker would be on an IRC channel. Not so anymore, with conventions like Defcon, Blackhat, and CanSecWest.
CanSecWest has an interesting contest. A hacking contest. The targets are the most common browsers: IE, Firefox, Chrome, and Safari. A new feature this year is the addition of smartphone hacking: Apple iOS, Windows Phone 7, Google Android, and BlackBerry OS. In total there is $125,000 in cash prizes. Another cool aspect of the competition: if you hack the computer running the target browser, you get to keep the laptop.
Like any good contest, there are the favorites. Charlie Miller, a software analyst from Baltimore has won the contest 3 times before. In 2009 Miller took down Safari running on an Apple in 10 seconds! He scored $10,000 and a laptop for his troubles. “Nils” (The contest allows anonymous entries) – a German computer science student, won last year, cracking Firefox, Safari, and Chrome in less than 10 minutes. In 2009, Nils broke the encryption for IE 8 the day before it was released, netting a new Sony laptop and $5k. George Hotz, the 21 year old who broke the Playstation 3’s copy protection (not to mention being the first person to ever jailbreak the iPhone) will be competing this year.
The biggest challenge this year is Google’s Chrome browser. Chrome runs in a ‘sandbox’ mode in Windows (basically insulating bugs in Chrome from affecting the underlying Windows system.) Google has put up $20,000 if someone can break Chrome’s sandbox mode in the first day.
Contests like this just aren’t cool in the computer security world. They provide vendors with information on how to improve the security of their products. When someone hacks a browser/device they also share technical information on how they did it with the contest organizers, TippingPoint. Details on the hacks aren’t released to the public until the vendor has time to fix the bug.
Pwn2Own runs during the CanSecWest conference, being held in Vancouver CA between March 9-11 2011.
Update: It looks like things are back to normal. But it was fun while it lasted in that, getting-drunk-and-saying-things-you-would-never-say-in-the-light-if-day way.

